Dynamic Multipoint VPN - 1
Thanks to these references, below. I followed the same steps to setup my lab. If you are looking for DMVPN, you should read them first. I also came across this information from 9tut.com which summaries DMVPN concept.
It is the combination of the following technologies:
+ Multipoint GRE (mGRE)
+ Next-Hop Resolution Protocol (NHRP)
+ Dynamic Routing Protocol (EIGRP, RIP, OSPF, BGP…) (optional)
+ Dynamic IPsec encryption (optional)
+ Cisco Express Forwarding (CEF)
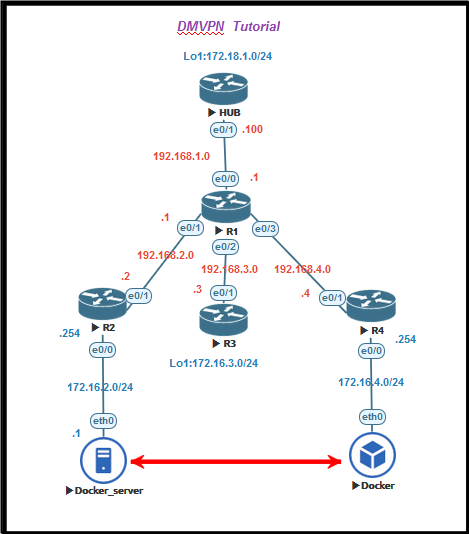
That is the lab which I used. One client on the right side, namely docker, is able to access to the server side. I do not post all explanation of command, since references, below, have more details. We need to know some basic encryption algorithm, HMAC, symmetric/asymmetric encryption, 3DES (Data Encryption Standard), Authentication Method( pre-shared key), Hash Algorithm(MD5)
hostname HUB
interface e0/1
ip address 192.168.1.100 255.255.255.0
no shut
ip route 192.168.2.0 255.255.255.0 192.168.1.1
ip route 192.168.3.0 255.255.255.0 192.168.1.1
ip route 192.168.4.0 255.255.255.0 192.168.1.1
=======================================
!!R1 configuration
hostname R1
interface e0/0
ip address 192.168.1.1 255.255.255.0
duplex full
no shut
interface e0/1
ip address 192.168.2.1 255.255.255.0
duplex full
no shut
interface e0/2
ip address 192.168.3.1 255.255.255.0
duplex full
no shut
interface e0/3
ip address 192.168.4.1 255.255.255.0
duplex full
no shut
=======================================
!!R2 configuration
hostname R2
interface e0/1
ip address 192.168.2.2 255.255.255.0
duplex full
no shut
interface loopback 0
ip address 172.16.2.1 255.255.255.0
duplex full
no shut
ip route 192.168.1.100 255.255.255.255 192.168.2.1
=======================================
!!R3 configuration
hostname R3
interface e0/1
ip address 192.168.3.3 255.255.255.0
duplex full
no shut
interface loopback 0
ip address 172.16.3.1 255.255.255.0
duplex full
no shut
ip route 192.168.1.100 255.255.255.255 192.168.3.1
=======================================
!!R4 configuration
hostname R4
interface e0/1
ip address 192.168.4.4 255.255.255.0
duplex full
no shut
interface loopback 0
ip address 172.16.4.1 255.255.255.0
no shut
ip route 192.168.1.100 255.255.255.255 192.168.4.1
!!HUB Configuration
interface Tunnel0
ip address 10.1.1.1 255.255.255.0
ip nhrp map multicast dynamic
ip nhrp network-id 1
tunnel source 192.168.1.100
tunnel mode gre multipoint
ip mtu 1416
=======================================
!!R2 configuration
interface Tunnel0
ip address 10.1.1.2 255.255.255.0
ip nhrp map 10.1.1.1 192.168.1.100
ip nhrp map multicast 192.168.1.100
ip nhrp network-id 1
ip nhrp nhs 10.1.1.1
tunnel source 192.168.2.2
tunnel mode gre multipoint
ip mtu 1416
=======================================
!!R3 configuration
interface Tunnel0
ip address 10.1.1.3 255.255.255.0
ip nhrp map 10.1.1.1 192.168.1.100
ip nhrp map multicast 192.168.1.100
ip nhrp network-id 1
ip nhrp nhs 10.1.1.1
tunnel source 192.168.3.3
tunnel mode gre multipoint
ip mtu 1416
=======================================
!!R4 configuration
interface Tunnel0
ip address 10.1.1.4 255.255.255.0
ip nhrp map 10.1.1.1 192.168.1.100
ip nhrp map multicast 192.168.1.100
ip nhrp network-id 1
ip nhrp nhs 10.1.1.1
tunnel source 192.168.4.4
tunnel mode gre multipoint
ip mtu 1416
=======================================
!!IPSEC configuration
crypto isakmp policy 10
hash md5
encryption 3des
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
crypto ipsec transform MINE esp-3des
crypto ipsec profile DMVPN
set transform-set MINE
interface tunnel0
tunnel protection ipsec profile DMVPN
=======================================
!!Dynamic Route configuration, except R1
interface tunnel0
ip hold-time eigrp 1 35
no ip next-hop-self eigrp 1
no ip split-horizon eigrp 1
router eigrp 1
network 192.168.0.0
network 172.16.0.0
network 10.0.0.0
no auto-summary
=======================================
debug nhrp
debug nhrp packet
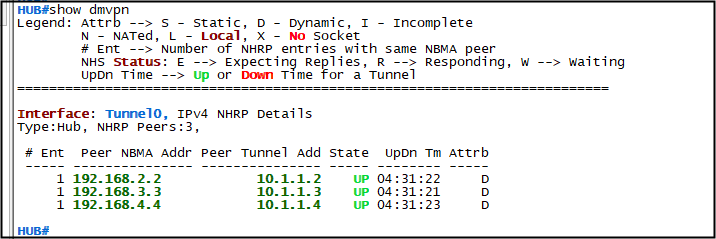
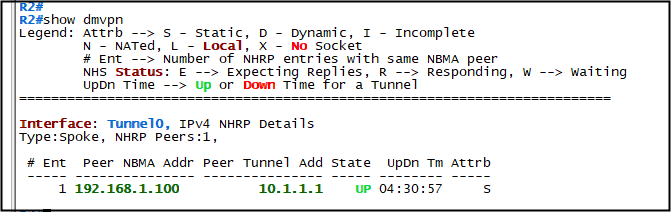
show dmvpn
show ip route
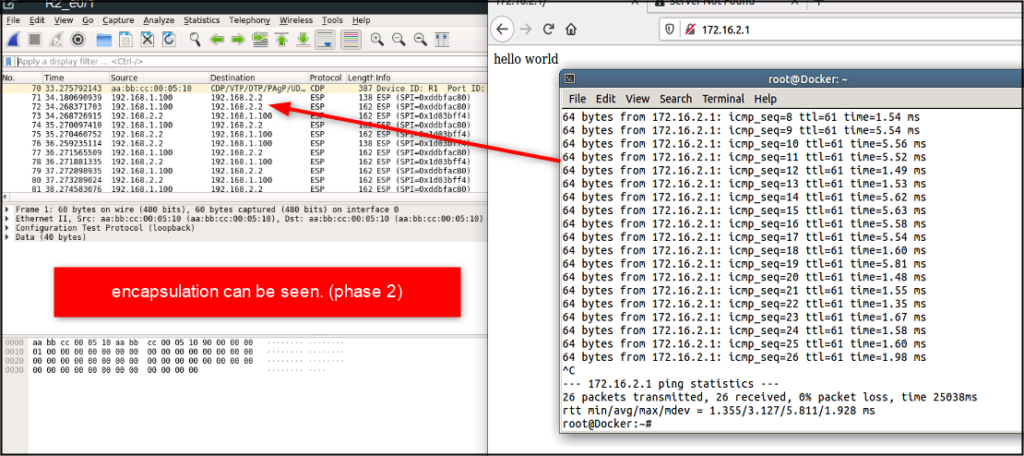
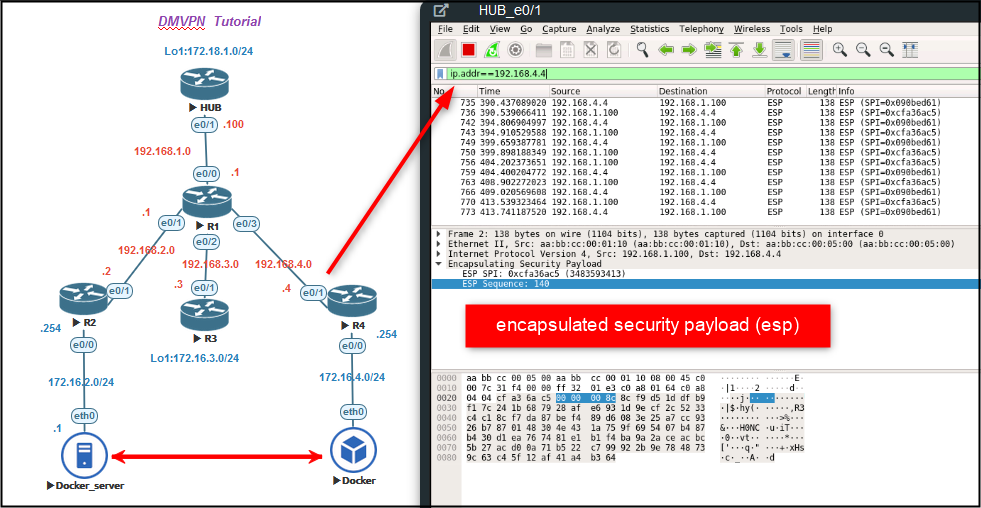
If we look at the packets on Wireshark, it is encrypted. IPsec configuration, including pre-shared key, above, supports encryption of all data.
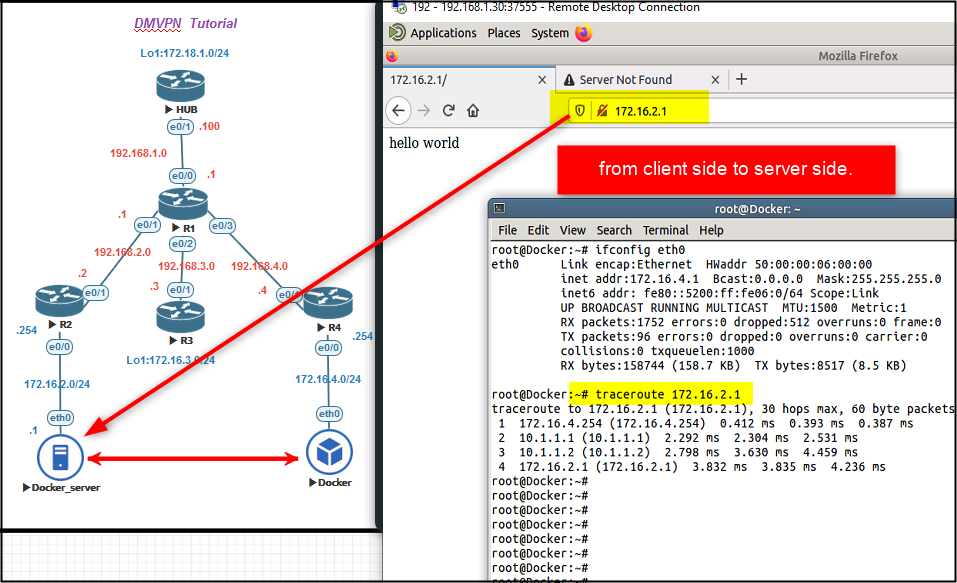
Ping from client side to server. This is phase 2, so only HUB IP address is seen as a source.